
You need three things for effective cybersecurity. Are you doing them?
You saw the headline, and you’re thinking to yourself, just three things? Is this some joke? Nope, when I say we need to have three things to have effective cybersecurity, it’s because it’s the truth. How you choose to do those three things will define how effective your cybersecurity is.
Can cybersecurity finally be that easy? Yes, it can, especially with help from your Millenium Micro Partner. The three things you need are a cybersecurity culture, security stack and backups.
Can it be that simple? I thought cybersecurity was incredibly complex and in the realm of I.T. security specialists. But, I guess that depends on your point of view; cybersecurity is indeed a vast subject that needs years to become an expert, but you don’t need to be an expert.
Think of your car; you know what you need and want in a vehicle, you have an idea of your budget and how you plan to use it. But, do you know about the 30,000 parts needed to build one or how each component works together to give you the ability to drive? Probably not, and that’s okay.
Spent the next five minutes with me, and let’s go over those three things you need for effective cybersecurity.
Cybersecurity Culture
In business, we often talk about the culture of the organization. The organizational culture helps us define the accepted norms, values and behaviours of our employees. It’s not a policy you can find on paper; it lives and breaths and changes with the needs of your business. It plays a role in absolutely everything you do, embraced by everyone from the big boss up top down to the summer intern. A great corporate culture will improve employee satisfaction and job performance.
Chances are, your business now runs on technology, and cybersecurity culture has to be a key component of your organization. So it’s more than just doing your occasional training; it’s about our behaviour and attitudes towards cybersecurity.
Increased security means changing our habits, like, not reusing passwords across multiple services or carefully examining an email before opening an unexpected attachment or link.
It also means how your I.T. department addresses cybersecurity needs to change as well. For example, they can’t simply hand out a policy and say, here, do this and expect compliance. After all, your employees don’t work for the I.T. department.
I.T. and cybersecurity policies should exist to support productivity, not reduce it. That means having a conversation about why a policy exists, the risks to productivity, and security risks. Unfortunately, it may mean the policy needs to be re-written or removed entirely!
Don’t believe me? Did you know that nearly every cybersecurity frameworks advise AGAINST regular password changes? For example, in 2017, the NIST passwords recommendations included not forcing users to change their passwords! Scheduled password changes were leading to weaker cybersecurity. People reused passwords, guessable patterns or were leaving them on post-it notes because of these constant changes.
Everyone needs to embrace cybersecurity as a positive complement to everyday work. That means having a conversation to help sensitize employees to risks, engage in training. Most importantly, discuss how to integrate cybersecurity without negatively impacting productivity.
Security Stack
A security stack is a series of software components that work together to provide you with layered security. Think of it as ordering a cheeseburger; nearly everyone knows what you mean. But, of course, what that cheeseburger tastes and looks like can change depending on where you buy it, your budget and how hungry you are.
Security stacks work the same way; they should have a few basics covered, but depending on your budget or need can vary differently.
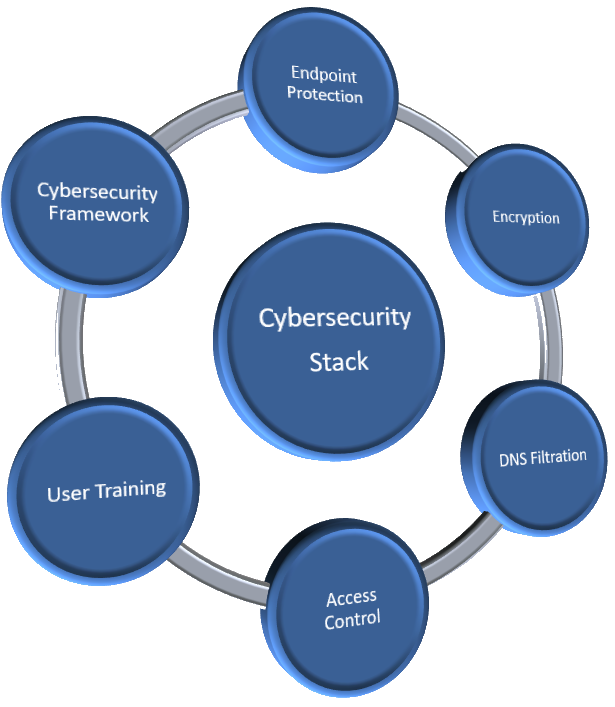
Basics for a good security stack are:
User Training
User training should be continuous ongoing training that effectively teaches new and emerging threats, often combined with phishing simulations.
Endpoint Protection
Also known as your antivirus/antimalware, and you should install it on all computers. Continuously running in the background, this defense layer comes in after opening a malicious link, app or document.
Encryption
Most computers and devices support encryption. If enabled, should the device be lost or stolen, you have significantly reduced your risk and liability for a PIPEDA or privacy breach.
DNS Filtration
Your firewall, antivirus or a 3rd party application will provide this. It blocks malicious websites from being opened. What is that saying? An ounce of prevention is better than a pound of cure.
Access Control
Software, policies and procedures all come together for access control. But, at its core, you want to make sure the right people have access to what they need and not the things they don’t. For example, if you have an H.R. person, they don’t get access to your bank accounts, so why would you let them access the finance data?
Cybersecurity framework
Adopting a cybersecurity framework reduces your cyber-risks. For a small business, two common ones that you can work with are the ‘NIST CSF’ and ‘Canadian Baseline Cyber Security Controls for Small and Medium Organizations.’ Think of them as a series of checkboxes to help you identify your current cybersecurity risks and stance.
The great part of a security stack is you don’t have to go it alone, a professional I.T. partner like Demand ITS can help you build a stack that works within your budget and level of risk.
Need help building a security stack? Schedule a 1 hour no obligation consult with Robert Picard here
Backups
It doesn’t matter how big your organization is; everyone is susceptible to data loss. Five of the most common reasons for data loss are :
- Accidental Deletion
- Intentional Deletion
- Attacks (Ransomware, Viruses, Malware)
- Disaster (Fire, Flood, System Failure)
- Device or credential theft
If you have data that’s important, you need to back it up no matter where it lives, including in the cloud. However, you may not realize that cloud vendors often state that they are not responsible for lost data in the end-user license agreement.
To secure your data, it helps to have backups. They should include your email, documents, and any line of business application regardless of where it exists. The great news is, Demand ITS Inc. can help here too! So you don’t need to go it alone.
Conclusion
Remember when I said you only needed three things for effective cybersecurity? A cybersecurity culture, security stack and backups.
How you go about doing these three things will define how effective your cybersecurity is. The great news is that if you’ve already mastered cybersecurity culture, you can outsource the rest!
If you need help with any stage of the cybersecurity journey, please reach out to us! Stay secure, stay safe!


